Request a Free Scan Account
Please complete the form to apply for a free scan account.
We'll get back to you as soon as possible.
Turaco Labs needs the information provided to contact you about our services.
Tags:
During a recent investigation into a compromised eCommerce website, a suspicious file modification was detected that coincided with the introduction of malware into the system. A file associated with WordFence, a popular security plugin for WordPress, had its size increased by a mere 39 bytes. An initial review did not reveal any obvious backdoor, which is commonly expected with such minor changes.
To pinpoint the exact modifications, a fresh copy of the WordFence plugin was downloaded for manual comparison. The team found that only two lines had been added to the file.
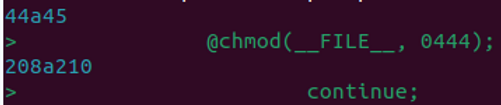
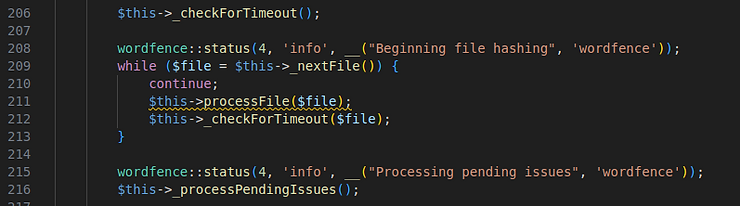
The first line, "@chmod(FILE, 0444);", changed the file permissions to read-only, preventing any further changes or updates. The second addition was a single "continue" statement, strategically placed within a while loop that processes each file on the filesystem during a scan. This placement caused the loop to skip processing entirely, effectively preventing the WordFence scanner from detecting any files. This enabled the criminals to load malicious code elsewhere in the site that would not trigger an alert in Wordfence.
This incident underscores the importance of File Integrity Monitoring (FIM). Such subtle modifications might appear harmless and would likely evade detection by traditional malware scanners.
However, with ThreatView Advanced, forensic-level analytics are built into the technology, enabling a full file change review within seconds. As an example, here is a screenshot of a change comparison of code within a file with malware inserted:

Proactive security. Simplified.
Article by Bhavin Patel, Foregenix Threat Intelligence Group
PrestaShop has recently issued a security alert warning store owners about a digital skimmer threat targeting their platform. If you're running a PrestaShop store, this is an important reminder to verify your site's security.
With growing numbers of clients hosting with WP Engine, we felt it may be useful to highlight how a WordPress eCommerce site security is handled by combining WP Engine and ThreatView.
TLDR: WP Engine gives you high-performance managed WordPress hosting. ThreatView Advanced makes sure your website stays secure.
It's Cyber Monday, following record-breaking Black Friday sales (according to Forbes magazine) and the Christmas rush is fast approaching - all with the backdrop of SessionReaper targeting Magento /Adobe Commerce sites and a significantly growing number of hacked sites worldwide.
As of this morning, we can see over 50,000 domains with indicators of compromise - with nearly 90% of the detected malware targeting eCommerce payment data.