Request a Free Scan Account
Please complete the form to apply for a free scan account.
We'll get back to you as soon as possible.
Turaco Labs needs the information provided to contact you about our services.
Tags:
The buzz around the new PCI DSS requirements for eCommerce is well-deserved - and for good reason.
The evolving threat landscape demands that businesses stay ahead, particularly in securing the checkout process (requirement 6.4.3) and monitoring all scripts loaded during that critical stage. This is a significant leap forward in combating the wave of cybercrime targeting eCommerce platforms.
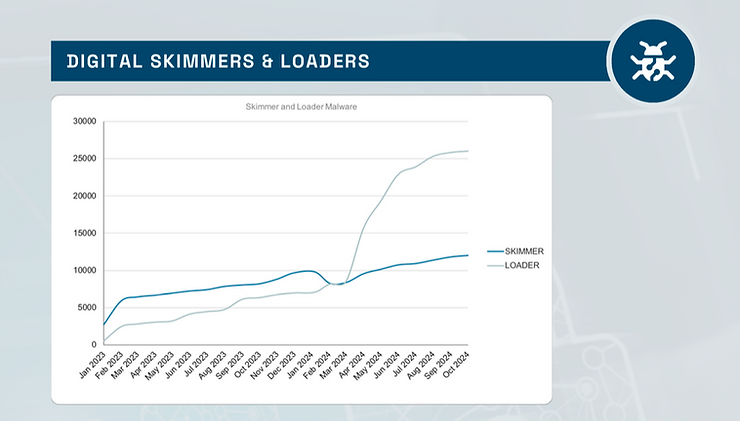
According to our latest eCommerce ThreatScape Report, March 2024 marked a notable shift in malware tactics, moving from digital skimmers to digital loaders.
Why does this matter?
In simple terms, the industry has largely caught up to detecting digital skimmers, prompting cybercriminals to adapt. To stay in business, they’ve developed a two-stage attack: deploying a seemingly harmless digital loader first, which then calls in a digital skimmer from another compromised domain. This innovation has caused a sharp increase in detected digital loaders—an area where our R&D and forensic teams excel in providing robust detection capabilities.
How does PCI DSS Requirement 6.4.3 help?
This requirement will drastically strengthen the defence for eCommerce sites.
Enter File Change Monitoring (Requirement 11.5.2) - a game-changing tool for understanding and responding to changes in your website’s filesystem.
Imagine this scenario:
But is it truly resolved?
Without deeper insights, you’re left wondering:
Unfortunately, many businesses find themselves in a costly game of cat and mouse, with hackers reinfecting sites within hours of cleanup. This is where a forensic-grade File Change Monitoring system becomes indispensable—and cost-effective.
How ThreatView Advanced Edition Helps:
Our solution offers a fully integrated File Change Monitoring system that meets PCI DSS Requirement 11.5.2, providing unparalleled control and insight. Key features include:
This powerful capability empowers your developers and agencies to save time, reduce costs, and effectively counter sophisticated cyberattacks.
With ThreatView Advanced Edition, you gain an out-of-the-box solution that simplifies security operations, supports PCI DSS compliance, and provides peace of mind for your eCommerce operations.
PrestaShop has recently issued a security alert warning store owners about a digital skimmer threat targeting their platform. If you're running a PrestaShop store, this is an important reminder to verify your site's security.
With growing numbers of clients hosting with WP Engine, we felt it may be useful to highlight how a WordPress eCommerce site security is handled by combining WP Engine and ThreatView.
TLDR: WP Engine gives you high-performance managed WordPress hosting. ThreatView Advanced makes sure your website stays secure.
It's Cyber Monday, following record-breaking Black Friday sales (according to Forbes magazine) and the Christmas rush is fast approaching - all with the backdrop of SessionReaper targeting Magento /Adobe Commerce sites and a significantly growing number of hacked sites worldwide.
As of this morning, we can see over 50,000 domains with indicators of compromise - with nearly 90% of the detected malware targeting eCommerce payment data.