Request a Free Scan Account
Please complete the form to apply for a free scan account.
We'll get back to you as soon as possible.
Turaco Labs needs the information provided to contact you about our services.
Tags:
At Turaco Labs, we have identified a live digital skimmer (e-skimmer) that hijacks Stripe Elements (and potentially other gateways) by proxying Stripe through a look-alike mirror system. A small and innocuous PHP code change quietly rewrites js.stripe.com to the attacker’s domain. From there, a transparent reverse-proxy spoofs headers and modifies responses while returning content that looks and behaves exactly like the real thing.
While most attacks that aim to replace the checkout payment flow with an attacker-controlled input or data harvesting function are easily spotted due to their notable differences from the expected payment workflow, MirrorMask maintains the look and feel of the original payment flow perfectly. This makes it significantly less likely to be detected by site owners and administrators.
Stripe Elements is widely - and rightly - considered a secure way to collect payment card data. It isolates card fields in iframes served directly by Stripe and requires merchants to verify the domains that embed Elements. Our discovery shows how a threat actor can appear to satisfy those checks by relaying traffic through a controlled mirror server. This keeps the checkout working and looking normal while quietly siphoning data in transit.
Important: We’ve seen no evidence of a weakness in Stripe’s platform. The compromise happens on the merchant site, where an attacker can rewrite resource URLs and then relay requests upstream.
As of mid-August 2025, the malicious domain we investigated had been in use for nearly two months and, to our knowledge, has not yet been flagged by any major vendors.
We’re referring to this technique as MirrorMask - the attacker presents a near-perfect reflection of Stripe’s public endpoints so that everything looks familiar to the browser and to the user.
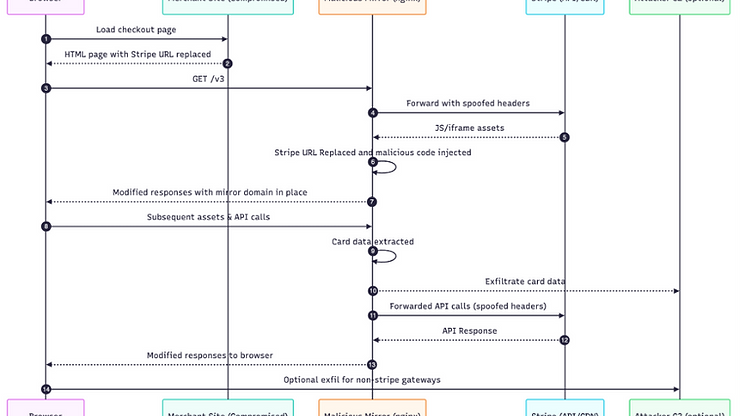
Stripe expects Elements to be embedded from known, verified domains. MirrorMask relays browser traffic so that requests arriving at Stripe look like they came from the legitimate site (thanks to header spoofing). Since the merchant site itself initiated the resource load (albeit to the mirror), everything else - the iframe structure, API paths, and runtime behavior - still matches expectations.
Again, it is important to note: This is not a bug in Stripe; it’s the consequence of local code tampering on the merchant’s site, plus a high-fidelity relay that keeps the rest of the contract intact.
Defender Note: We’re deliberately avoiding step-by-step configs that would help reproduce the attack. The above is enough to understand and mitigate without enabling abuse.
Note on SRI: Subresource Integrity is powerful but can be hard to use with third-party libraries that change frequently. Treat CSP as your primary line of defense here.
Toward the end, a little product talk - because this is exactly what we built ThreatView to catch:
If you’d like help deploying CSP or scanning your checkout for MirrorMask-style issues, ThreatView can get you there quickly.
This article aims to inform defenders and merchants. It does not include step-by-step configurations that would facilitate abuse. We have no indication of a vulnerability in Stripe; the technique relies on a local content rewrite plus a high-fidelity relay.
In conclusion, the threat posed by MirrorMask is significant. eCommerce businesses must remain vigilant. Implementing robust security measures is essential. We protect online businesses. Our ThreatView product offers forensic-level file integrity monitoring and industry-leading malware detection. We bring over 20 years of payment industry forensic investigation expertise to secure your operations. Ensure your PCI DSS compliance and safeguard your online business.
PrestaShop has recently issued a security alert warning store owners about a digital skimmer threat targeting their platform. If you're running a PrestaShop store, this is an important reminder to verify your site's security.
With growing numbers of clients hosting with WP Engine, we felt it may be useful to highlight how a WordPress eCommerce site security is handled by combining WP Engine and ThreatView.
TLDR: WP Engine gives you high-performance managed WordPress hosting. ThreatView Advanced makes sure your website stays secure.
It's Cyber Monday, following record-breaking Black Friday sales (according to Forbes magazine) and the Christmas rush is fast approaching - all with the backdrop of SessionReaper targeting Magento /Adobe Commerce sites and a significantly growing number of hacked sites worldwide.
As of this morning, we can see over 50,000 domains with indicators of compromise - with nearly 90% of the detected malware targeting eCommerce payment data.