Request a Free Scan Account
Please complete the form to apply for a free scan account.
We'll get back to you as soon as possible.
Turaco Labs needs the information provided to contact you about our services.
Tags:
With the new PCI DSS Requirement 6.4.3 for eCommerce sites, much is being said around client-side security solutions to meet the PCI DSS Requirements and to combat digital skimming attacks. However, despite the hype, they fall short of being the industry's "silver bullet".
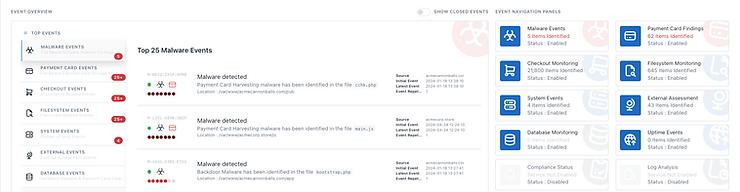
Comprehensive eCommerce Security Monitoring - ThreatView Advanced Edition
Client-side security solutions monitor your website's front-end code as it runs in your customer's browsers. These tools use JavaScript sandboxing and behavior analysis to identify and block potentially malicious code. Well marketed solutions include offerings from Human Security, SourceDefense, JScrambler and Reflectiz.
When malicious code appears on your website, it indicates your infrastructure has already been compromised. While client-side protection might neutralize some malicious frontend code, it doesn't prevent attackers from infiltrating your system initially. Once attackers gain server access, they control:
Effective security should focus on preventing and/or detecting unauthorized access to your systems, not just limiting potential damage after a breach occurs.
While Client-side security tools make sense as a layer within a multi-layered defence, they should not to be treated as a standalone Silver Bullet, even with all the fanfare that is currently going with the new PCI 6.4.3 requirements.
Why?
When attackers control your server, they can easily:
Vendors of client-side security often highlight supply chain attacks in their marketing - scenarios where criminals compromise trusted third-party service providers used by multiple merchants.
While these attacks are concerning, especially in light of recent events, our experience and data still shows that they are rare - yes, there have been multiple attacks in the last few years and security solutions should certainly be monitoring for these threats. But in comparison with direct server compromises, the supply chain attacks are currently a "much rarer event".
At Turaco Labs, our global monitoring shows digital skimming attacks have increased 6-fold over the past two years, affecting hundreds of thousands of online stores - yet only a small percentage involved third-party services. Again, Let me re-iterate, this threat should not be ignored and a security solution should be monitoring for these supply chain threats/issues; but in the context of our global stats, supply chain attacks in the eCommerce world are a much rarer event than the usual suspects.
To effectively protect against digital skimming, take a multi-layered approach:
If you're still considering a client-side solution to "tick your PCI 6.4.3 box", perhaps ask potential vendors this critical question: "What does your solution do to prevent my store from being hacked in the first place?"
Focus your security on applying a multi-layered defence to your business - where you are able to monitor for threats and protect your online business using comprehensive security.
PrestaShop has recently issued a security alert warning store owners about a digital skimmer threat targeting their platform. If you're running a PrestaShop store, this is an important reminder to verify your site's security.
With growing numbers of clients hosting with WP Engine, we felt it may be useful to highlight how a WordPress eCommerce site security is handled by combining WP Engine and ThreatView.
TLDR: WP Engine gives you high-performance managed WordPress hosting. ThreatView Advanced makes sure your website stays secure.
It's Cyber Monday, following record-breaking Black Friday sales (according to Forbes magazine) and the Christmas rush is fast approaching - all with the backdrop of SessionReaper targeting Magento /Adobe Commerce sites and a significantly growing number of hacked sites worldwide.
As of this morning, we can see over 50,000 domains with indicators of compromise - with nearly 90% of the detected malware targeting eCommerce payment data.